If there ever were a digital poison that people have been consuming for a very long time, without knowing the cyber dangers it posed, it would be CCleaner. This software has been highly recommended for so many years when you find your computer bogged down with cache, incorrectly uninstalled applications, and generally to speed up things on a slow computer.
You can imagine users’ surprise when it was unveiled that CCleaner despite doing some remarkable performance improvement on a slow computer. It also doubled up as a malware and spyware.
It is now emerging that the CCleaner malware was more sophisticated than it had earlier been believed; this revelation came after CCleaner was established to be a malware in the first place. Days following the unearthing of CCleaner as a super stealthy malware, security researchers have been poring through its data from the seized command and control center.
Hackers were using CCleaner remotely for espionage
The researchers found evidence that the attackers were exploiting the compromise and used it to target big-time companies such as Microsoft, Google, and Samsung among others. Security firm Avast and Cisco’s Talos research group have detailed in a blog post of vulnerabilities that came with CCleaner.
When the servers were being seized, it was discovered that the attackers were after a string of internal domains via a second-stage payload designed for purposes of collecting data and giving hackers a constant backdoor to the infected devices.
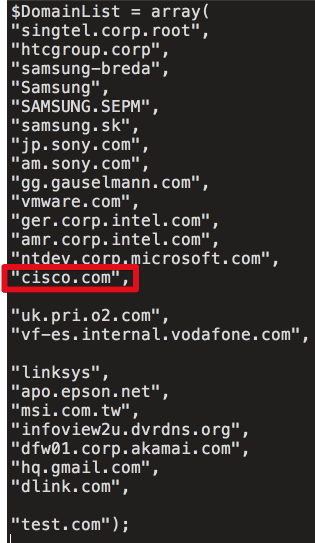
Talos published a list of domains attacked by CCleaner. The list includes ‘ntdev.corp.microsoft.com,’ which is an internal domain for Microsoft’s Windows developers. There was also the ‘hq.gmail.com’ used by Google employees. The big tech companies whose domains are in this list include Samsung, Sony, Intel, and Akamai.
This list only includes domains for the companies targeted during the four days before the CCleaner servers were seized. Hence it is highly possible that more companies had been targeted earlier on.
The hackers were not interested in ‘small fish’
Nonetheless, the nature of the two-stage payload strongly suggests that the attacks were not just arbitrarily. The hackers were targeting particular companies rather than attacking the millions of computers running the application at once. That is probably why it went for so long without getting noticed, it acted like a choosy lion at the watering hole, taking precautions not to spoke the animals it was uninterested in, but waiting patiently for a particular prey to come by.
Security researchers now say that only about 700,000 computers were attacked. A smaller figure from the 2.2 million that was earlier estimated. As to which specific companies were successfully hacked remains to be established.
Talos has established at least 20 computers that were attacked by the payload, but they fell short of naming names of the individual companies affected. It has also not been established what the hackers were after. Although according to Talos, the nature of the attack on a specific domain could imply the hackers were very much focused on valuable intellectual properties.
So far no notorious hacking group has made claims of the work. However, researchers at the Kaspersky Labs say there is an overlap in the code used in the CCleaner attack and that of a previous attack perpetrated by the Axiom threat group. Talos also agrees with Kaspersky’s assertions.
Was China involved?
The Axiom group has been (allegedly) linked to the Chinese intelligence service. Security experts are yet to get down to the bottom of the CCleaner malware threat. Data from the initial command server has so far revealed that other servers were also used in this attack. Law enforcement agencies are currently working to locate and seize these servers.