The internet has become an essential part of our daily lives, and we rely on it for various activities. However, the convenience of the internet has a downside. Our privacy and anonymity are at risk. Whenever we use the internet for communication, shopping, and banking, we leave a digital trail that can be traced back to us. Therefore, it is crucial to protect our privacy and anonymity online.
This article will provide 10 tips to safeguard your online privacy and remain anonymous while browsing the internet.
Part 1. Exploring Various Methods of Maintaining Online Anonymity
Nowadays, it is very important to keep your online identity safe in this era. Considering the vast quantity of personal data easily accessible online, protecting our privacy has become imperative. Thankfully, there are several ways to maintain our online anonymity.
These include using virtual private networks (VPNs), the Tor network, antidetect browsers, and tools for anonymous web browsing. All of these are discussed in detail below, along with a few other methods that might work best for you in the long term:
1.1 VPN
Using a Virtual Private Network (VPN) is a potent solution if you want to maintain anonymity while surfing the internet. By encrypting your internet traffic and redirecting it through a server located elsewhere, a VPN can make it challenging for anyone to trace your online movements. There is a plethora of VPN services available, both free and paid.
However, it’s crucial to research the service before settling on one to ensure it caters to your requirements. Once you’ve established a connection to the VPN server, your internet traffic will be encrypted and channeled through it. While a VPN can help keep you anonymous, logging into personal accounts can still reveal your identity.
1.2 Tor Browser
Tor Browser allows users to browse the internet anonymously. It uses a network of servers to route internet traffic, making it difficult for anyone to track a user’s online activity, including their location and IP address. This browser encrypts your internet traffic, making it difficult for anyone to monitor your online activity, including your internet service provider, government agencies, and hackers.
The Tor network is an alternative option for anonymous internet browsing, ensuring that your online activities cannot be traced back to you. This can be useful if you’re trying to protect your identity or avoid surveillance. Moreover, some countries or organizations may block certain websites or online services. By using the Tor browser, you can access these sites even if they are blocked in your location.
1.3 Proxy Server
A proxy server is an intermediary between your devices, such as Windows PC, Mac, Android, or iOS, and the internet. When you connect to the internet through a proxy server, all your internet traffic flows through the server first before reaching its destination. Your Internet Service Provider (ISP) assigns a unique identifier called an IP address to your device when you connect to the internet. However, using a proxy server can obscure your IP address.
Occasionally, specific websites and services are limited to regions. Using a proxy server located in the region where the website or service is available, you can bypass those geographic restrictions and access the content you want. This can be particularly useful when using public Wi-Fi, which is often insecure and can be easily intercepted.
1.4 Pseudonym
Using a pseudonym or a false name is another way to stay anonymous online. Unlike a proxy server, which masks your IP address and encrypts your internet traffic, using a pseudonym simply involves choosing a different name to use online instead of your real name. It can help protect your privacy online by preventing others from knowing your real name.
Unfortunately, the internet can be a hostile and dangerous place, and some people may use personal information to harass or stalk others online. Using a pseudonym can make it more difficult for someone to track you down and harass you. It can also help protect your reputation online by preventing others from associating your real name with controversial or embarrassing content.
1.5 Anti-Detect Browser
An anti-detect browser is a specialized browser designed to help users stay anonymous on the internet by hiding their digital footprint. These browsers are typically used by individuals who want to protect their online privacy, avoid tracking by advertisers, or access websites that may be restricted in their region. They often include built-in security features that protect users from malware and phishing attacks.
Anti-detect browsers such as MoreLogin are designed to protect users from browser fingerprinting, trackers websites and advertisers use to track users based on their unique browser configuration. This browser uses various techniques to make it difficult for websites to track users, including blocking cookies, disabling browser plugins, and spoofing browser information.
1.6 Secure Operating System
Secure OS can provide several benefits for those who wish to stay anonymous on the internet. They are designed to prevent hacking and protect your personal information from being stolen and use advanced encryption techniques to ensure that your online activity remains private and secure. A secure operating system can help you remain anonymous online by hiding your IP address and other identifying information.
It can also help you bypass censorship and access blocked websites. This can be especially important if you live in a country where internet freedom is restricted. Using a secure OS can assist in protecting your privacy by preventing third-party tracking and monitoring of your online activity. This can help prevent companies from collecting and using your personal data for targeted advertising.
1.7 Disable Cookies and Tracking
This method helps to protect your online privacy by preventing websites and advertisers from tracking your online activity, collecting data about you, and building a profile based on your browsing behavior. Without tracking and cookies, advertisers won’t be able to serve you targeted ads based on your browsing behavior. This can be beneficial for those who find targeted advertising invasive or distracting.
Moreover, disabling cookies and tracking gives you greater control over your personal information by preventing websites and advertisers from collecting your data without your consent. Some websites rely heavily on cookies and tracking scripts to load, which can slow down browsing. Disabling these scripts can improve website loading times and improve your overall browsing experience.
1.8 Privacy-Focused Search Engine
These search engines do not track your online activities, which means your personal information is not collected or sold to third parties. This means you can get a more diverse range of search results and avoid being trapped in a filter bubble. They often use encrypted connections to protect your searches from interception and eavesdropping. This can help protect your sensitive information from being compromised.
Some privacy-focused search engines use alternative algorithms that focus on providing more accurate and relevant search results. This can lead to a better experience overall. It is important to note that no search engine can guarantee complete privacy and anonymity online. However, using a privacy-focused search engine can help reduce your digital footprint and make it harder to track your online activities.
1.9 Be Cautious About Sharing Personal Information
Cybercriminals can use personal information such as your name, address, and date of birth to steal your identity and commit fraud in your name. Sharing personal information online can also lead to an invasion of privacy, where your personal information can be used for targeted advertising or even sold to third-party advertisers. That is why you should be cautious while sharing such information.
Moreover, sharing too much personal information on social media platforms or other websites can make you an easy target for cyberstalking and online harassment. Many online companies collect and store personal information, which can be vulnerable to data breaches. If a data breach occurs, your personal information could be exposed, potentially harming you.
1.10 Two-Factor Authentication
To strengthen account security, two-factor authentication requires users to provide two forms of identification before accessing their accounts or data. This added layer of protection enhances online anonymity, making it more difficult for malicious actors to impersonate users or gain unauthorized access to their accounts. It is especially crucial for users seeking to safeguard their online identities.
However, should two-factor authentication be enabled, hackers would need to gain access to the user’s phone or other physical devices to complete the login process, making it substantially more difficult for them to impersonate the user or obtain sensitive information.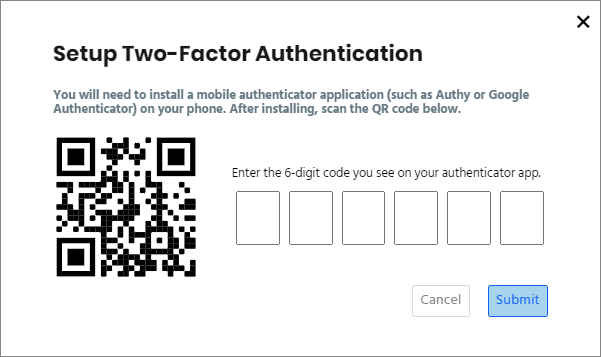

Part 2. Top-Notch Anti-Detect Browser to Maintain Anonymity
MoreLogin is a unique anti-detect browser designed to bypass the detection mechanisms of websites, allowing users to remain undetected while surfing the internet. This browser is equipped with advanced features that make it difficult for websites to track users and gather personal information. Moreover, it also allows you to create unlimited profiles to manage all your social media and business accounts in one place.
Furthermore, additional features this browser offers include multiple account management, bulk cookie import, team collaboration, and an affiliate marketing program, which pays a 15% commission on every sale. The MoreLogin is built on the Chromium framework and enables easy importing of browser extensions from Chrome.
It is compatible with Windows and Mac operating systems and offers a flexible pricing model that allows users to scale up as needed. Paid users have access to premium features, such as website automation, Robotic Process Automation (RPA), team collaboration, profile sharing, and automatic proxy matching. In addition, MoreLogin supports profile storage and recycling, among other features.
Key Features Offered By MoreLogin for Every User
As a unique anti-detect browser, it offers a wide range of features not commonly found in similar browsers. Here are a few of its key features:
- Effective Fingerprinting Protection: This browser uses enhanced fingerprinting protection techniques to prevent websites from identifying your device and tracking your online activity. This includes protecting against browser fingerprinting, canvas fingerprinting, and other techniques used by websites to track users.
- Rotation of User-Agent: It automatically rotates the user agent used by the browser to make it more difficult for websites to track your online activity. This can help you stay anonymous online and avoid being identified by websites that use user agent tracking.
- Multiple Browser Profiles: MoreLogin allows you to create and manage multiple browser profiles, each with its unique fingerprint. This can be useful if you need to use different identities online or want to keep your personal and work browsing separate.
- Browser Settings for Customization: You can also freely customize various browser settings, including browser language, time zone, screen resolution, and more. This can help you create a more realistic online persona and avoid detection by websites that look for inconsistencies in your browser settings.
Steps to Download and Use MoreLogin Promptly
Below are the detailed steps so that the user can easily download and use this anti-detect browser as per their needs:
Step 1: Install the Package and Register Account
Go to MoreLogin’s official website and download the package for free after creating the account. Once you install the package and register yourself by following the guidelines, click on the “New Profile” button at the screen’s top-left corner.

Step 2: Customize the Settings
Choose your “Browser” and “Operating System” under the “Short Cut Creation” tab. Enter the number of profiles you want to create under the “Profile Number Created” section. Click “Ok” at the bottom of the screen to create a browser successfully.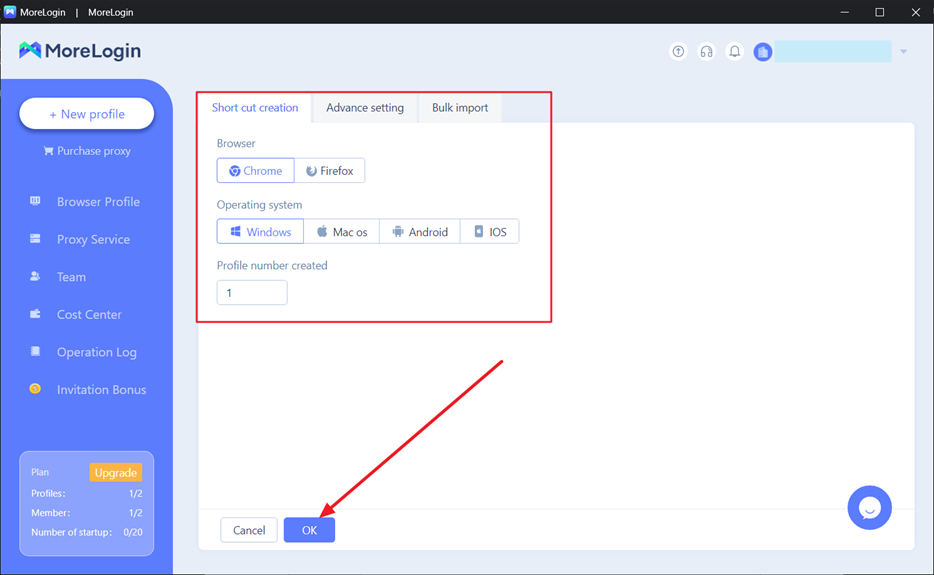

Step 3: Activate the Browser
After you have completed the previous step, Click on the “Start” button to activate the new browser. Now, you can browse anything without worrying about your data leak or identity revealing.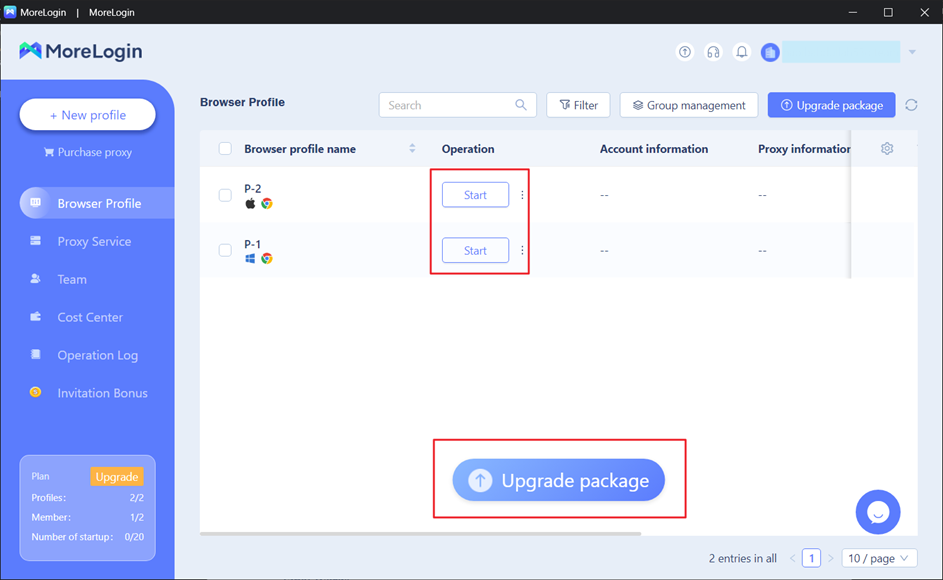

Final Words
The internet has become an integral part of our lives, and we cannot deny its immense benefits. However, with the increased internet use, our online privacy and anonymity have become major concerns. Incorporating the ten above-mentioned strategies for safeguarding your online privacy and anonymity can significantly mitigate the threat of cyber-attacks and protect your data.
One tool that can help you maintain your online privacy and anonymity is the MoreLogin anti-detect browser, designed to keep your online activities private and secure by masking your IP address.



